Leverage Cloud Solutions for Enhanced Information Protection
In today's digital landscape, the ever-evolving nature of cyber threats necessitates a proactive method towards safeguarding delicate information. Leveraging cloud solutions presents a compelling option for companies looking for to strengthen their data protection steps. By handing over reputable cloud company with information management, organizations can use a riches of protective features and cutting-edge technologies that bolster their defenses against destructive stars. The inquiry arises: how can the use of cloud solutions change information security practices and offer a durable shield versus possible susceptabilities?
Importance of Cloud Safety
Making sure durable cloud protection procedures is extremely important in guarding sensitive data in today's digital landscape. As companies increasingly depend on cloud solutions to keep and refine their data, the need for solid safety and security methods can not be overemphasized. A breach in cloud protection can have severe effects, ranging from economic losses to reputational damages.
One of the primary reasons why cloud safety is vital is the common duty model employed by most cloud solution carriers. While the copyright is accountable for safeguarding the infrastructure, consumers are accountable for protecting their information within the cloud. This division of responsibilities underscores the significance of implementing robust safety and security steps at the individual level.
In addition, with the proliferation of cyber hazards targeting cloud settings, such as ransomware and information violations, organizations should stay cautious and proactive in mitigating risks. This entails consistently upgrading safety and security procedures, checking for dubious tasks, and enlightening staff members on ideal techniques for cloud protection. By focusing on cloud protection, companies can much better shield their delicate information and promote the trust fund of their stakeholders and consumers.
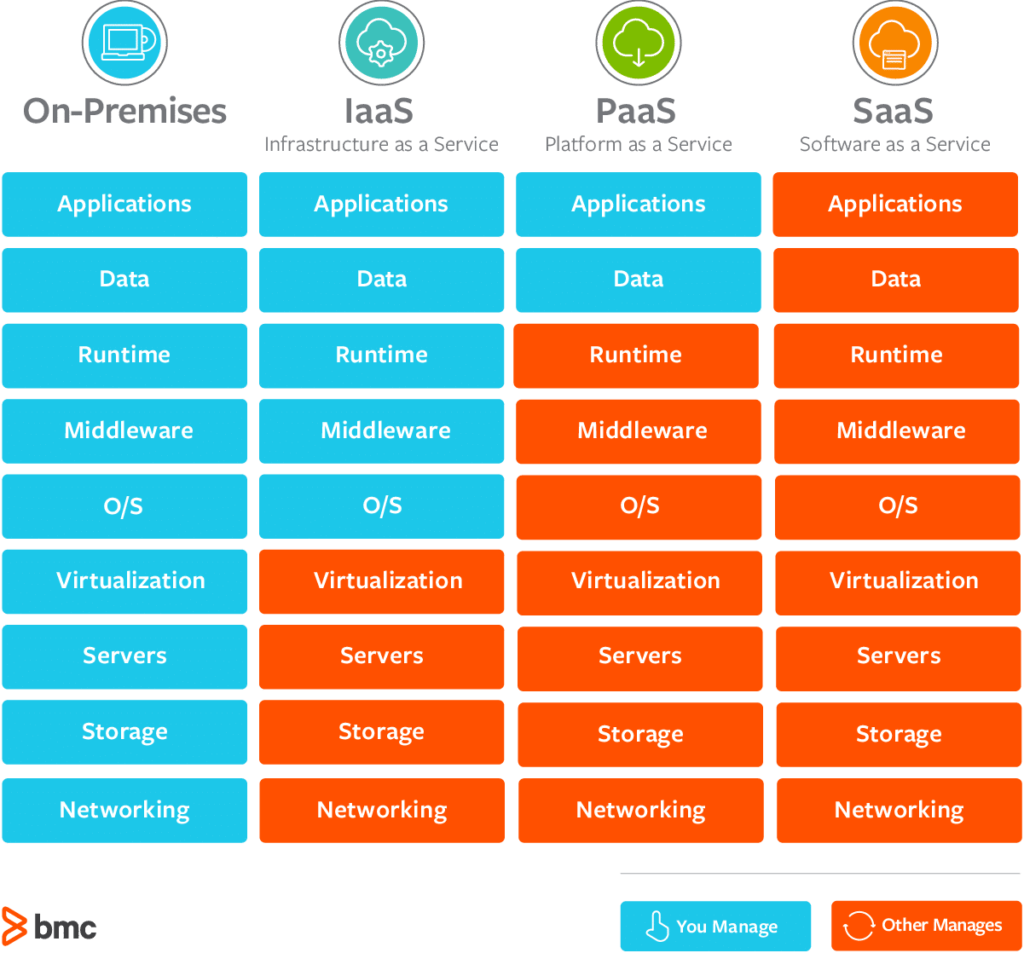
Information Security in the Cloud

Security in the cloud commonly entails the usage of cryptographic formulas to rush data right into unreadable styles. Additionally, lots of cloud solution providers supply encryption mechanisms to secure information at rest and in transportation, improving general data security.
Secure Data Backup Solutions
Data back-up options play a critical duty in making certain the strength and safety of data in the occasion of unforeseen events or data loss. Safe and secure data backup solutions are important parts of a durable data protection method. By on a regular basis backing up information to protect cloud servers, organizations can minimize the threats connected with data loss due to cyber-attacks, equipment failings, or human mistake.
Carrying out protected data backup solutions find more involves picking reliable cloud company that supply security, redundancy, and information stability steps. File encryption guarantees that data stays protected both en route and at rest, securing it from unapproved accessibility. Redundancy systems such as data duplication throughout geographically dispersed servers assist stop total data loss in instance of web server failings or all-natural catastrophes. Additionally, information stability checks guarantee that the backed-up information stays tamper-proof and unchanged.
Organizations ought to develop computerized back-up timetables to ensure that data is regularly and effectively supported without hands-on treatment. When needed, regular screening of information reconstruction procedures is additionally critical to assure the performance of the back-up services in recovering data. By purchasing safe and secure information backup options, services can improve their data safety and security position and minimize the impact of potential information violations or interruptions.
Function of Gain Access To Controls
Executing stringent access controls is important for maintaining the security and honesty of delicate info within business systems. Accessibility controls work as an essential layer of defense against unapproved access, ensuring that just authorized individuals can view or adjust sensitive data. By specifying who can access details resources, companies can limit the risk of information breaches and unauthorized disclosures.
Regularly assessing and updating accessibility controls is necessary to adapt to organizational adjustments and advancing safety risks. Continuous surveillance and auditing of access logs can aid find any dubious tasks and unapproved gain access to attempts promptly. Generally, robust accessibility controls are essential in protecting sensitive information and mitigating safety and security threats within organizational systems.
Conformity and Regulations
Routinely ensuring conformity with relevant regulations and criteria is necessary for organizations to promote data security and personal privacy measures. In the world of cloud services, where information is typically visite site stored and processed on the surface, adherence to industry-specific guidelines such as GDPR, HIPAA, or PCI DSS is important. Cloud Services.
Cloud company play a vital function in aiding organizations with compliance efforts by using solutions and features that line up with various governing needs. For instance, many suppliers supply file encryption capacities, access controls, and audit routes to help companies fulfill data safety criteria. Furthermore, some cloud solutions go through normal third-party audits and accreditations to show their adherence to sector laws, offering included assurance to organizations looking for certified options. By leveraging certified cloud solutions, organizations can improve their data safety posture while meeting regulatory obligations.
Verdict
Finally, leveraging cloud services for enhanced information protection is necessary for companies to protect sensitive details from unauthorized accessibility and potential violations. By implementing durable cloud protection procedures, consisting of data file encryption, secure back-up solutions, gain access to controls, and conformity with policies, organizations can benefit from sophisticated protection procedures and experience provided by cloud solution suppliers. This aids minimize dangers effectively and makes certain the privacy, integrity, and schedule of information.
Information back-up remedies play a critical duty in making sure the strength and safety of information in the event of unexpected incidents or information loss. By on a regular basis backing up information to secure cloud web servers, companies can reduce the risks linked with information loss due to cyber-attacks, hardware failures, or human mistake.
Executing secure information backup services involves selecting reputable cloud service providers that supply file encryption, redundancy, and data integrity measures. By investing in safe and secure information backup options, companies can enhance directory their information security pose and minimize the effect of potential data violations or disruptions.
 Josh Saviano Then & Now!
Josh Saviano Then & Now! Mike Vitar Then & Now!
Mike Vitar Then & Now! Erik von Detten Then & Now!
Erik von Detten Then & Now! Bo Derek Then & Now!
Bo Derek Then & Now! Peter Billingsley Then & Now!
Peter Billingsley Then & Now!